Businesses of all types get targeted by cyber criminals, and Banks and financial institutions are no different. As an Managed Service Provider (MSP) that specializes in IT services & cybersecurity for banks and credit unions, we train our clients’ employees to spot phishing attempts because it’s one of the most popular and successful attack vectors for cyber criminals.
Introduction – The First Phishing Attack
Truth be told, Phishing has been around for quite a long time. In fact, it even predates the era of the Internet Bubble, which occurred in the mid to late 90’s. The first known Phishing attack that was made public happened to AOL, in 1999. There was a hacker group known as “The Warez Community”, and this even considered to be the first true breed of “Phishers”.
In their plot against AOL, they created a mathematical algorithm which would guess at random, any of the credit card numbers that were currently being used by the subscribers to AOL. If there was indeed a specific match, this group of Cyberattackers could then very easily replicate an authentic account and make it into a phone one. From here, they were then able to spam the other AOL subscribers into giving up their Personal Identifiable Information (PII).
But AOL was able to prevent this type of hacking to continue, but “The Warez Community” further crafted their trade, in that they moved onto more, other sophisticated forms of Phishing attacks, such as pretending to be legitimate employees (this is also considered to be one of the earlier examples of Social Engineering), and sending out authentic looking, but phony AOL instant messages to other subscribers.
Because of the gravity of these new threat variants, the term “Phishing” became officially coined and adopted on January 2nd, 1996. Well, fast forward to over two decades later, and Phishing still remains to be the dominant Cyberthreat that still prevails today. Compared to the mid 90’s, the Phishing variants have become sophisticated, it is almost impossible to tell what a real Email message is, or for that matter, even a legitimate website.
But keep in mind that every Cyberattacker, no matter how stealthy they might be, always leaves behind even the most minute trails of evidence, which takes a trained eye to pick up on. The goal of this article is to give you some tips to help you pick up those minor nuances so that you will be able to discriminate what is a real Email message and a phony one.
The Telltale Signs
So, what are the signals that you need to pick up on to tell if an Email is a Phishing based one, or for that matter, even if a website is not a spoofed one? Here are some clues:
The Email does not make use of a legitimate domain name:
Every legitimate business or organization always has their own domain name from which they use to host their website and to send Emails from. Examples of this include such domains as “Microsoft.com”, “Oracle.com”, “Cisco.com”, etc. In these instances, the user id will either be one of the following:
- The complete first and last name of an individual, that is separated by a dot. For example, John.Doe@microsoft.com.
- The first letter and the complete last name, like jdoe@microsoft.com.
- The first name and the first letter of the last name, such as johnd@microsoft.com.
- Just the first name of the individual, like john@microsoft.com.
In a Phishing based Email, a company domain is not used, or some concoction of it is actually used, in order to trick the person receiving the Email that it is a legitimate domain name. The reason for that is, people do not take a second a look at the domain name of the sender, just a cursory glance of it, it at all. Instead, we are much more focused upon the name of the sender. So for example, the sender of a spoofed Email may look something like microsoft@support.com, or even John.Doe@microsoftt.com (notice the extra “t” at the end). This is also illustrated in the example below:
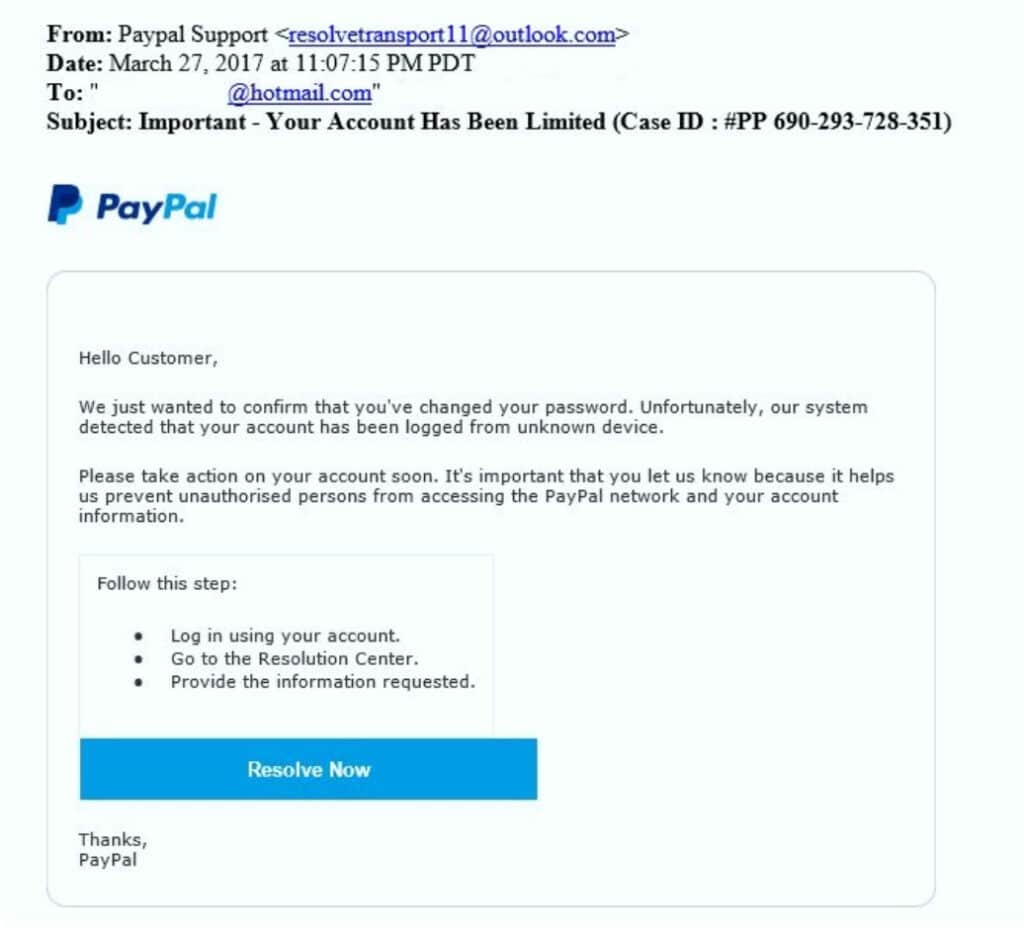
As it is clearly evident, the name of the sender looks very legitimate. But even a closer look reveals that the standard Email naming convention is way off, thus giving you the first indication that this is Phishing Email. In other words, the Email address should also consist of the name of the sender in some format, as it was reviewed earlier. Thus, it is always important to check for both syntaxes.
There are numerous spelling and/or grammatical mistakes in the body of the Email message:
Apart from the phony E-Mail address, the next major clue to give you an indication that an Email is a Phishing based one is that there are grammar and spelling mistakes in the actual composition of the Email. In order to totally evade the untrained eye, the Cyberattacker will most likely misspell just a few words or use improper grammar at random locations in the text of the Email so that they will be difficult to spot at first glance.
The illustration below clearly demonstrates this:
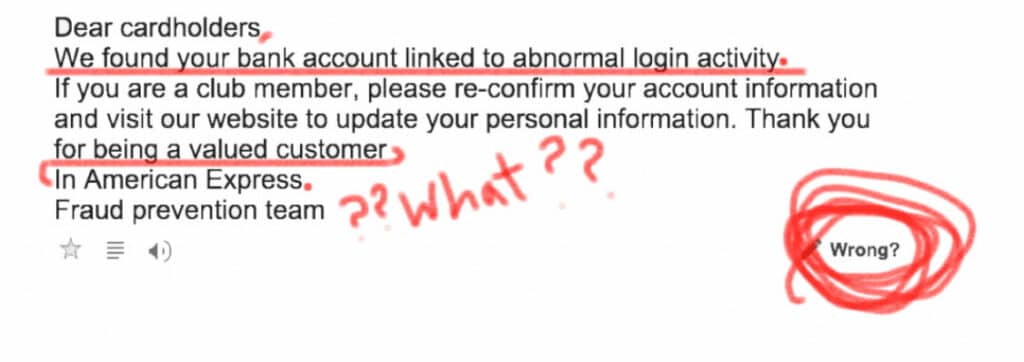
As it can be seen, there are two missing periods , and the line break at the last sentence is totally way off. Thus, it is especially important to keep in mind that grammatical mistakes simply just do not involve poor wording. It also includes missing punctuation marks, which can be also difficult to spot at first glance. If there are any doubts, you can simply copy and paste the content of the E-Mail into a Word document and do a spell/grammatical check. This feature in Word has become very sophisticated, so it will be able to pick up on even the most minor nuances. After you run the spell/grammatical check, any errors will be quickly seen. After closer inspection, if there are any spelling or grammatical nuances that seem out of the ordinary, then this is your second major clue that you have received a Phishing Email.
There is a sense of urgency that is created:
Most Phishing Emails, somewhere in the body of the message, will have a call to action that requires an immediate response of sorts. For example, it may be to reset your password, or log into an account in order to check for fraudulent activity (in this regard, you will be taken to a spoofed, but authentic looking website). Most of these relate to financial institutions because these are probably some of the ones that strike the most fear in us if we are alerted to the fact that is something is wrong. A typical example of this is PayPal.
This is illustrated in the example below:
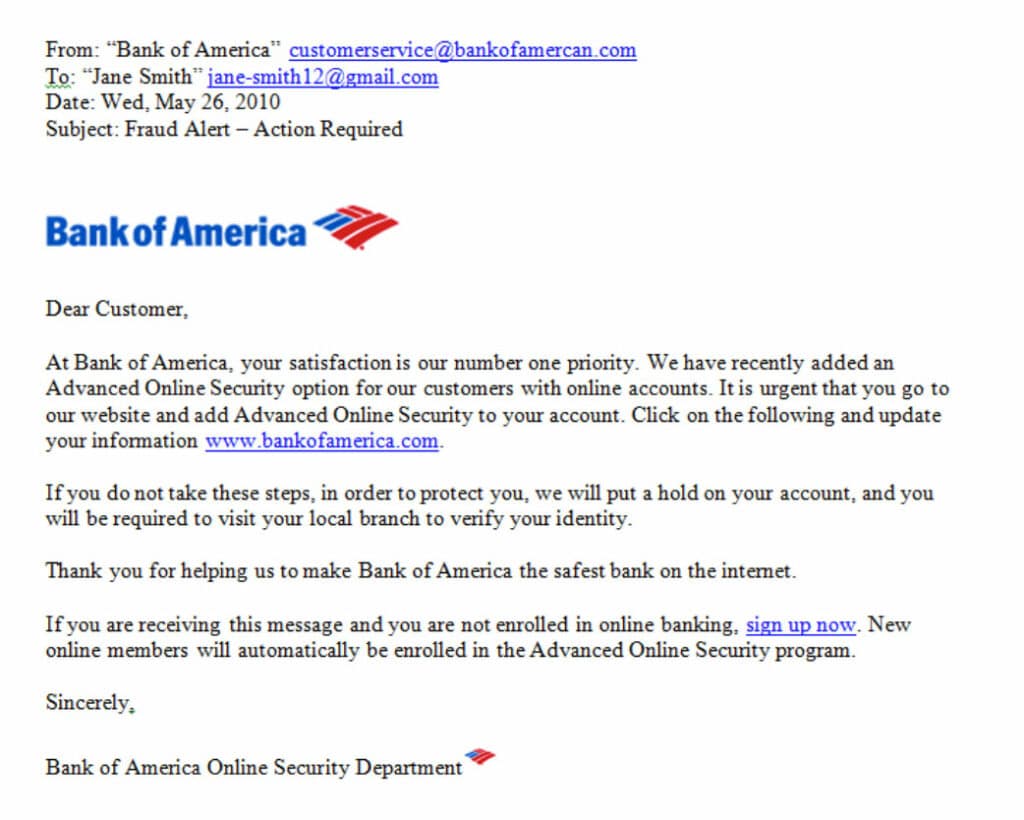
As it is demonstrated, there are two urgent call to actions, one at the end of the first paragraph, and the other fourth paragraph. It is particularly important to keep in mind in this instance, that any legitimate financial institution will never ask you to do anything like this in an Email, or for that matter, even in a phone call. Normally, these kinds of notifications are normally sent via snail mail, to your home address, alerting you to the fact that your online account may have indeed been compromised. This is the third warning sign of what a Phishing Email could potentially look like.
Malicious links are present:
Most, if not all, Phishing based Emails will either contain a malicious link or even a malicious attachment for you to download. In the case of the latter, most of these attachments come in the form of either .XLS (Excel), .PPT (PowerPoint), .DOC (Word), and even .PDF file extensions. In these instances, these files will typically consist of hidden macros which contain the malware. Once the attachment has been downloaded and opened, the malware then spreads itself very rapidly to the device of the victim. Thus, it is very crucial to use some sort of either antivirus and/or antimalware software package in your Email reader to scan these documents first for any signs of malware, viruses, or even Trojan Horses. As an extra security step, if you are not expecting to receive any attachments, contact the sender of the Email to see if they have actually sent the Email. If they have not, then you for certainty that you have received a Phishing Email.
Now, along with the malicious attachment, the Phishing Email will also have a malicious link to it as well. It can come either in the form of a direct link, or it can also embedded into an image of the Email message. This is illustrated below:
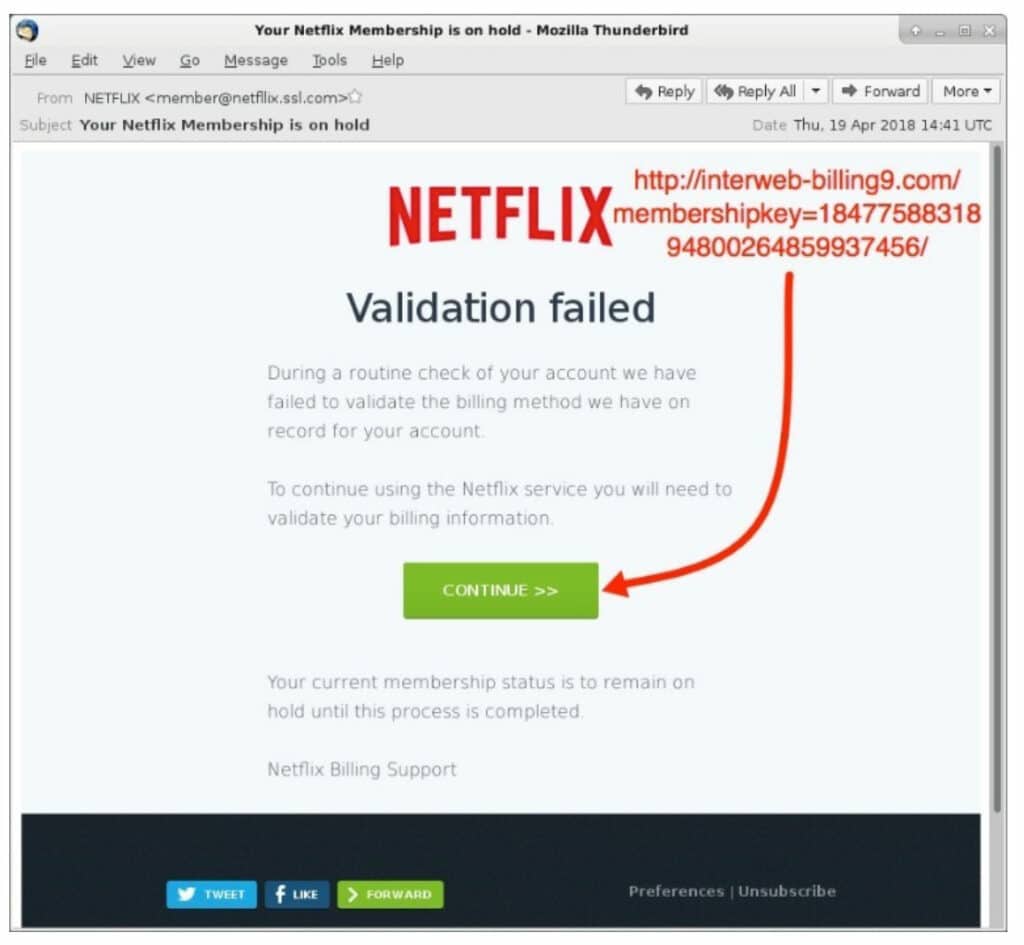
In the green box above, if you hover your mouse over it, the link should originate from Netflix.com. But as it is clearly evident, it does not. If there is any mismatch like this, this is also a clear indication (and 4th) that you have received a Phishing Email. Therefore, before you click on any links, always hover your mouse over it to see if there are variances. If there are, then do not under any circumstances click on that particular link.
The Email does not include your name in it:
Any legitimate Email, when it is initially sent, will typically address you by your first name, or perhaps even both your first and last name as well. Even automated Emails that are used in mass Email marketing campaigns will address you by your name as well. But typically, Phishing Emails do not do this, which is illustrated below:
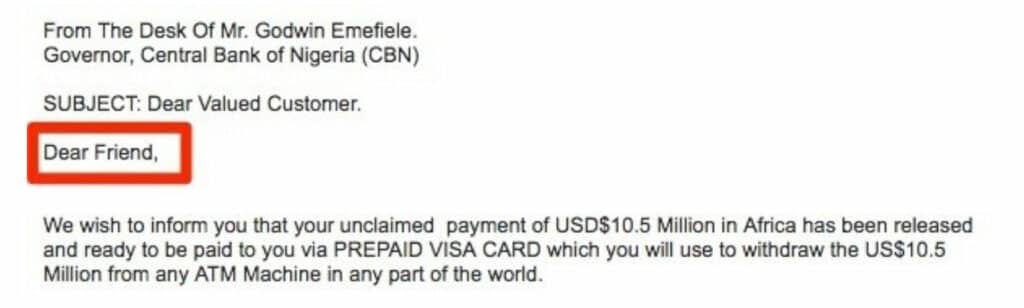
But there are Phishing Emails that will also use your name as well, in a fashion that seems a little bit out of the ordinary, for example, instead of saying “Dear John”, it will say something like “Dear JohnDoe” or even “DearJohnDoe”. If you notice any of these types of discrepancies, you know then you have received a Phishing Email, and this is your 5th indication.
Conclusions
Overall, this article has examined five key indicators of a Phishing based Email. There are others as well, and a simple Google search will point to them as well. So, in the end, what is the best line of defense? The bottom line is always trust your gut. If something does not feel right, it probably is not. Simply delete the Email message, and notify your immediate boss about it, so that the IT Security team can take the appropriate actions to mitigate the risk of happening again.
Sources


